Cybercriminals have been selling anti-virus (AV) and Endpoint Detection and Response (EDR) solutions killers as a method to propagate malware evading detection.
Vx-underground posted their latest AV and EDR killer hours without another requirement popped up. According to a demo posted by a cybersecurity researcher, the AV and EDR killers helped the user escape detection.
Furthermore, the seller of the AV and EDR killer moreover boasted of it stuff capable of impacting Extended Detection and Response (XDR).
Details of the AV and EDR killers sold on the visionless web
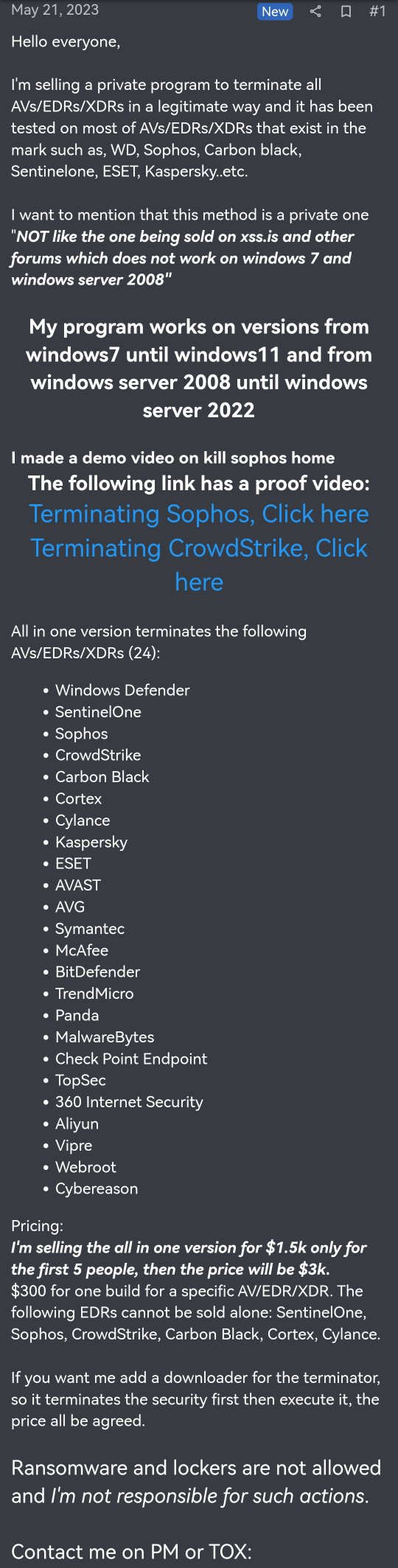
“I am selling a private program to terminate all AVs/ EDRs/ XDRs in a legitimate way and it has been tested on most of Avs/ EDRs/ XDRs that exist in the mark(et) such as WD, Sophos, Carbon black, SentinelOne, ESET, Kaspersky, etc,” the endorsement by a threat two-face by the name Spyboy read.
(Photo: Soufiane/ Twitter)
The seller testified well-nigh the effectiveness of the AV and EDR killer on Windows 7 and Windows Server 2008, which was not possible with the one’s sold on xss.is and other forums.
The AV/ EDR/ XDR killer could evade detection on versions from Windows 7 until Windows 11 and from Windows Server 2008 to Windows Server 2022.
They posted two videos demonstrating how the AV/ EDR killer evaded Sophos and CrowdStrike detection as shown below:

Screenshot of the video showing the AV killer evading detection
Addressing the mention of Sophos in the video, Dennis Griffin, the VP of Engineering at Sophos clarified, “FYI, the video is of Sophos Home, which is not at all representative of our commercial product for businesses.”
Another reader wrote that the AV/ EDR/ XDR killer was too unseemly to be true.
AV/ EDR killer on sale, where would it work?
Spyboy named several solutions that the AV and EDR killer evaded in order to compromise its security and potentially offer wangle to cyber criminals. They were –
- Cortex
- Cylance
- Kaspersky
- AVAST
- AVG
- Symantec
- McAfee
- BitDefender
- TrendMicro
- Panda
- Malwarebytes
- CheckPoint Endpoint
- TopSec
- 360 Internet Security
- Aliyun
- Vipre
- Webroot
- Cybereason

Screenshot of the video showing evasion from Sophos Home
The all-in-one version of the AV/ EDR killer was charged $1,500 for the first five buyers. Pursuit that, its forfeit would increase to $3,000.
“$300 for one build for a specific AV/EDR/XDR,” Spyboy wrote well-nigh selling the AV killers individually. They widow that Specific EDR killers would not be sold vacated including the ones for SentinelOne, Sophos, CrowdStrike, Carbon Black, Cortex, and Cylance.

Screenshot of the AV and EDR killer program tabbed Terminator.exe
They plane mentioned a downloader for the terminator that would first disable the security and then execute it. These were misogynist on PM or TOX for negotiation.
A user on Twitter responded to the requirement of its effectiveness by stating that it is not as daunting as it seems to appear. Because the AV and EDR killer files would require to be run as an administrator which not all users can, readily.

Screenshot showing the AV/ EDR/ XDR killer in the process of evading detection by CrowdStrike
VX-Underground to launch its AV/EDR killer program
Cybersecurity researcher from VX-Underground noticed the AV and EDR killer in the visionless web and spoken that they will moreover launch their own version of it.
Their tweet read, “We have seen a trend in Threat Actors selling AV/EDR killers. We have decided to unveil our own AV/EDR killer program,” with the pursuit screenshot –
The Cyber Express reached out to VX-Underground for comments well-nigh them unveiling their own program for evading detection. We will update the vendible without receiving their response.
AV, EDR and XDR killers
AV killers are offensive and malicious security solutions that disables virus protection programs. It allows malware to enter systems while moreover evading firewall protection in some instances.
Dubbed AuKill, Sophos X-Ops stated that EDR processes are killed by these tools by exploiting outdated versions of the driver. EDR killers disable EDR detection and moreover help in deploying a backstairs for hackers to connect with commands on the target’s systems.
XDR helps detect attacks within a network largest than most EDRs could. It could help collect information from several threat vectors. AN XDR killer can pose a hair-trigger threat to enterprise security which increasingly often relies heavily on detection tools including AV/EDR/XDR.