Social networks are constantly rival inauthentic bot finance that send uncontrived messages to users promoting scam cryptocurrency investment platforms. What follows is an interview with a Russian hacker responsible for a series of warlike crypto spam campaigns that recently prompted several large Mastodon communities to temporarily halt new registrations. According to the hacker, their spam software has been in private use until the last few weeks, when it was released as unshut source code.

Renaud Chaput is a freelance programmer working on modernizing and scaling the Mastodon project infrastructure — including joinmastodon.org, mastodon.online, and mastodon.social. Chaput said that on May 4, 2023, someone unleashed a spam torrent targeting users on these Mastodon communities via “private mentions,” a kind of uncontrived messaging on the platform.
The messages said recipients had earned an investment credit at a cryptocurrency trading platform tabbed moonxtrade[.]com. Chaput said the spammers used increasingly than 1,500 Internet addresses wideness 400 providers to register new accounts, which then followed popular finance on Mastodon and sent private mentions to the followers of those accounts.
Since then, the same spammers have used this method to ventilate increasingly than 100 variegated crypto investment-themed domains. Chaput said that at one point this month the volume of bot finance stuff registered for the crypto spam wayfarers started overwhelming the servers that handle new signups at Mastodon.social.
“We suddenly went from like three registrations per minute to 900 a minute,” Chaput said. “There was nothing in the Mastodon software to snift that activity, and the protocol is not designed to handle this.”

One of the crypto investment scam messages promoted in the spam campaigns on Mastodon this month.
Seeking to proceeds a temporary handle on the spam wave, Chaput said he transiently disabled new worth registrations on mastodon.social and mastondon.online. Shortly without that, those same servers came under a sustained distributed denial-of-service (DDoS) attack.
Chaput said whoever was overdue the DDoS was definitely not using point-and-click DDoS tools, like a booter or stresser service.
“This was three hours non-stop, 200,000 to 400,000 requests per second,” Chaput said of the DDoS. “At first, they were targeting one path, and when we obstructed that they started to randomize things. Over three hours the wade evolved several times.”
Chaput says the spam waves have died lanugo since they retrofitted mastodon.social with a CAPTCHA, those squiggly letter and number combinations designed to stymie streamlined worth megacosm tools. But he’s worried that other Mastodon instances may not be as well-staffed and might be easy prey for these spammers.
“We don’t know if this is the work of one person, or if this is [related to] software or services stuff sold to others,” Chaput told KrebsOnSecurity. “We’re really impressed by the scale of it — using hundreds of domains and thousands of Microsoft email addresses.”
Chaput said a review of their logs indicates many of the newly registered Mastodon spam finance were registered using the same 0auth credentials, and that a domain worldwide to those credentials was quot[.]pw.
A DIRECT QUOT
The domain quot[.]pw has been registered and x-rated by several parties since 2014, but the most recent registration data misogynist through DomainTools.com shows it was registered in March 2020 to someone in Krasnodar, Russia with the email write edgard011012@gmail.com.
This email write is moreover unfluctuating to finance on several Russian cybercrime forums, including “__edman__,” who had a history of selling “logs” — large amounts of data stolen from many bot-infected computers — as well as giving yonder wangle to hacked Internet of Things (IoT) devices.
In September 2018, a user by the name “” (phonetically “Zipper” in Russian) registered on the Russian hacking forum Lolzteam using the edgard0111012@gmail.com address. In May 2020, Zipper told flipside Lolzteam member that quot[.]pw was their domain. That user advertised a service tabbed “Quot Project” which said they could be hired to write programming scripts in Python and C .
“I make Telegram bots and other rubbish cheaply,” reads one February 2020 sales thread from Zipper.
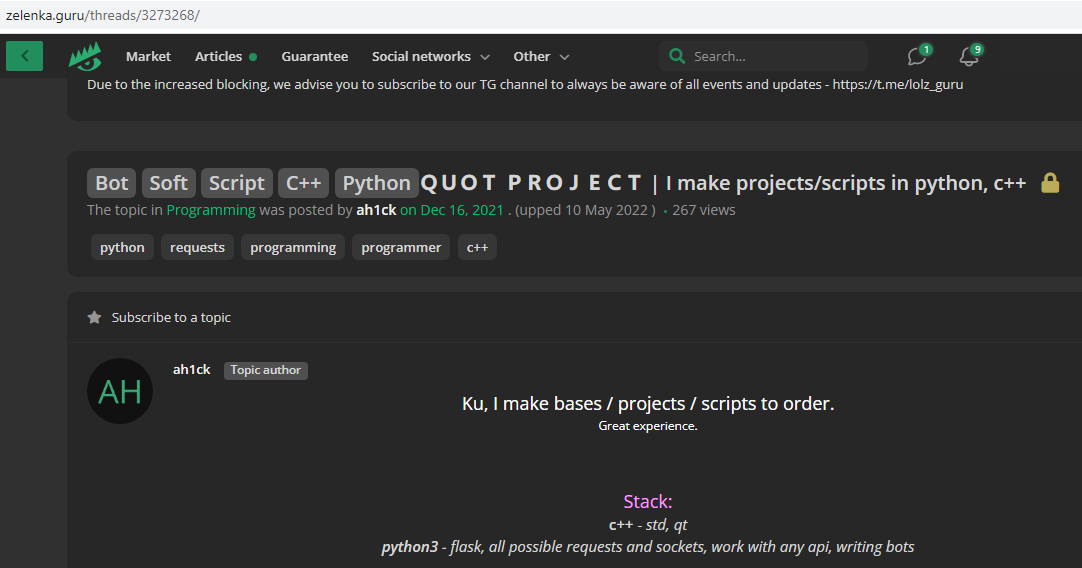
Quotpw/Ahick/Edgard/ razzmatazz his coding services in this Google-translated forum posting.
Clicking the “open yack in Telegram” sawed-off on Zipper’s Lolzteam profile page launched a Telegram instant message yack window where the user Quotpw responded scrutinizingly immediately. Asked if they were enlightened their domain was stuff used to manage a spam botnet that was pelting Mastodon instances with crypto scam spam, Quotpw confirmed the spam was powered by their software.
“It was made for a limited whirligig of people,” Quotpw said, noting that they recently released the bot software as unshut source on GitHub.
Quotpw went on to say the spam botnet was powered by well increasingly than the hundreds of IP addresses tracked by Chaput, and that these systems were mostly residential proxies. A residential proxy often refers to a computer or mobile device running some type of software that enables the system to be used as a pass-through for Internet traffic from others.
Very often, this proxy software is installed surreptitiously, such as through a “Free VPN” service or mobile app. Residential proxies moreover can refer to households protected by compromised home routers running factory-default credentials or outdated firmware.
Quotpw maintains they have earned increasingly than $2,000 sending roughly 100,000 private mentions to users of variegated Mastodon communities over the past few weeks. Quotpw said their conversion rate for the same bot-powered uncontrived message spam on Twitter is usually much higher and increasingly profitable, although they conceded that recent adjustments to Twitter’s anti-bot CAPTCHA have put a crimp in their Twitter earnings.
“My partners (I’m programmer) lost time and money while ArkoseLabs (funcaptcha) introduced new precautions on Twitter,” Quotpw wrote in a Telegram rely. “On Twitter, increasingly spam and crypto scam.”
Asked whether they felt at all conflicted well-nigh spamming people with invitations to cryptocurrency scams, Quotpw said in their hometown “they pay increasingly for such work than in ‘white’ jobs” — referring to legitimate programming jobs that don’t involve malware, botnets, spams and scams.
“Consider salaries in Russia,” Quotpw said. “Any spam is made for profit and brings illegal money to spammers.”
THE VIENNA CONNECTION
Shortly without edgard011012@gmail.com registered quot[.]pw, the WHOIS registration records for the domain were reverted again, to msr-sergey2015@yandex.ru, and to a phone number in Austria: 43.6607003748.
Constella Intelligence, a visitor that tracks breached data, finds that the write msr-sergey2015@yandex.ru has been associated with finance at the mobile app site aptoide.com (user: CoolappsforAndroid) and vimeworld.ru that were created from variegated Internet addresses in Vienna, Austria.
A search in Skype on that Austrian phone number shows it belongs to a Sergey Proshutinskiy who lists his location as Vienna, Austria. The very first result that comes up when one searches that unusual name in Google is a LinkedIn profile for a Sergey Proshutinskiy from Vienna, Austria.
Proshutinskiy’s LinkedIn profile says he is a Class of 2024 student at TGM, which is a state-owned, technical and engineering school in Austria. His resume moreover says he is a data science intern at Mondi Group, an Austrian manufacturer of sustainable packaging and paper.
Mr. Proshutinskiy did not respond to requests for comment.
Quotpw denied stuff Sergey, and said Sergey was a friend who registered the domain as a birthday present and favor last year.
“Initially, I bought it for 300 rubles,” Quotpw explained. “The extension forfeit 1300 rubles (expensive). I waited until it expired and forgot to buy it. Without that, a friend (Sergey) bought [the] domain and transferred wangle rights to me.”
“He’s not plane an information security specialist,” Quotpw said of Sergey. “My friends do not vest to this field. None of my friends are engaged in scams or other woebegone [hat] activities.”
It may seem unlikely that someone would go to all this trouble to spam Mastodon users over several weeks using an impressive number of resources — all for just $2,000 in profit. But it is likely that whoever is unquestionably running the various crypto scam platforms advertised by Quotpw’s spam messages pays handsomely for any investments generated by their spam.
According to the FBI, financial losses from cryptocurrency investment scams dwarfed losses for all other types of cybercrime in 2022, rising from $907 million in 2021 to $2.57 billion last year.



